kanep
Administrator
I have another new NDI tool to release, this one is helpful in troubleshooting NDI discovery. NDI Source Discovery, will scan your NDI network and display sources that appear using mDNS and Discovery Server methods. Each is displayed separately, so you can verify the method of discovery being used by the device.
Each source is displayed with its channel name, IP address, port and NDI group(s). You can even see sources in groups that you aren't receiving.
In the list of sources, you can double click it open it in NDI Studio Monitor. Or hold down shift and double click to open it in NDI Analysis. You will have to be in the same NDI group as the source in order to perform these functions.
 kanelp7.wixsite.com
kanelp7.wixsite.com
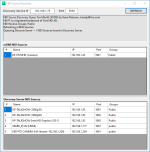
Each source is displayed with its channel name, IP address, port and NDI group(s). You can even see sources in groups that you aren't receiving.
In the list of sources, you can double click it open it in NDI Studio Monitor. Or hold down shift and double click to open it in NDI Analysis. You will have to be in the same NDI group as the source in order to perform these functions.
NDI Source Discovery | kanesworld

